
Approaches on Internet of Things Solutions
2013
Journal of Mobile, Embedded and Distributed Systems 5(3) 124-129
http://jmeds.eu/index.php/jmeds/article/view/105
Bucharest, Romania
Abstract: The Internet of Things (IoT) ecosystem is presented with its features and particularities in the first
section of the paper. In the second section are presented the technical terminology and how inter-domain
technologies such as: Internet/Semantic and Middleware, RFID/NFC and Smart Objects-embedded devices are
linked together. The paper shows an implementation of the authentication procedure with a proximity tag/card
implemented in Java SE, in the third section. The conclusions are presented in the fourth section and they
describe the opportunity to develop a proof of concept project, which may have multiple implementations.
Key-Words: Sensors Authentication, IoT (Internet of Things), Supply Chain Management Security
1. IoT (Internet of Things) Ecosystem Intro
The concept of Internet of Things (IoT) is related
to uniquely identifiable objects and their virtual
representations in a structure similar with the
Internet [1]. This new concept is an innovative
solution to realize a quantitative analysis of all
the things that surround us. A prerequisite
needed for the Internet of Things is the radiofrequency identification (RFID). If all objects and
people in real life were equipped with identifiers
and smart-tags, they could be managed and
inventoried by computers [2].
People have limited time, attention and accuracy,
so that they are not very good at capturing and
storing information about all the things from the
real world (even if we include 2D barcodes used
for Automatic Data Acquisition applications). An
alternative view on IoT, from the Semantic Web
perspective, focuses instead on making all things
addressable by the existing naming protocols,
such as URI (this refer to other things than those
electronic, smart, or RFID-enabled). The objects
themselves can be referred for the moment by
other agents, for example by powerful centralized
servers acting for their human owners, without
conversion.
In [3] is considered that the Internet of Things is
the network of physical objects that contain
integrated technology to communicate and sense
or to interact with their internal states or the
external environment.
The Internet of Things is a revolutionary concept
that is for the moment at the beginning, in the
incipient phase, but which will become in few
years an important research subject.
Figure 1 below present the concept of Internet of
Things and the connection between all involved
components.
For the development of all the applications of the
Internet of Things is compulsory to develop a
range of technologies and solutions, in which
free and open software plays an important role,
providing both hardware architecture and open
source software, such as development
environments, that allows the development of
open source applications for the Internet of
Things.
2. IoT Technical Details
The IoT is composed of many sensors,
application platforms, user platforms, and so on,
creating a community ecosystem. A sensor is a
component that collects and delivers information
about things in a specified area. By building a
shared common platform such as IoT will create
a richer ecosystem for all the people, by enabling
the development of innovative systems to focus
on the value-added of the human physical touch
points of connected objects and the services that
manage these objects [4].
The Internet of Things means to connect in realtime people and objects from the real physical
world together in a network of sensing,
reasoning, and action. The IoT connects people
and things together with software products and
applications.
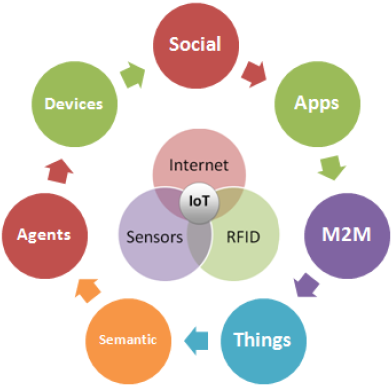
Figure 1. Internet of Things components
A Smart Object contains IoT data and
information, also metadata and software agent
code resources, such as application software
event handler. Samples of Smart Objects are
embedded devices such as Rasberry Pi,
Arduino, BeagleBone/Ninja Blocks. The data model for broad interoperability is represented
by the Smart Object API.
The Smart Object API is represented by a
Semantic Web application for the Internet of
Things that provides linked-data interactions
between application software agents and IoT
endpoints, sensors and user devices, which are
pluggable in real-time [5].
The IoT vendor silos provide high level cooked
APIs from cloud services of Smart Object API,
enabling integration of IoT resources from top to
bottom of the stack. The IoT of today means no
interoperability and existence of many vertical
and horizontal silos.
The Smart Object API supports the concept of a
Smart Gateway, which is working as a Smart
Object intermediate for devices on the network,
adding semantic descriptors and offering a
service interface for the device representation on
the Internet. Sensors and gateways must be
programmed for each service they need to
interact with.
IoT applications consist of sensors and actuators
end points, user device end points, and
application software that connect the endpoints
in the representation of a directed graph. We can
also build a graph of resources consisting of
Smart Objects connected to services and other
Smart Objects, based on the related IoT
ontologies, and the Smart Object API [6].
The
interoperability and
interdependence
between multiple devices is becoming a common
characteristic because people are trying to build
their own Internet of Things by getting all their
smart devices to be connected in the cloud. The
IoT needs a standard to interact with other
devices and this standard must enable software
for easier interaction.
The actual Internet of Things consists of many
different sensor networks and protocols,
connected to special cloud services and offering
access through smart mobile devices and
browser applications. It is unusual for these
separate silos to cooperate or interact one with
each other [7].
Figure 2 describe the Internet of Things tech
items grouped on three main categories: Internet
– Protocols – Middleware, Sensors – RFID,
Embedded Devices – Smart Objects.

Figure 2. Internet of Things tech items
The Internet of Things has many applicability
areas and fields, such as the healthcare
sector, the retail sector, transportation
services, educational services, industry and so
on.
Due to the large applicability of Internet of
Things, experts agree that the opportunities
presented by the Internet of Things are
endless, as it becomes easier and easier to
bring physical objects online. A practical
example is represented by different smart
devices connected on a social network for
machines that will help homes to save energy
[8].
Figure 3 presents the simplified schema of IoT
home saving energy example.
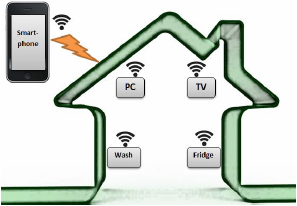
Figure 3. IoT home saving energy example
As we can see from Figure 3, the online
network of physical objects is realized by using
RFID tags and some other types of sensors.
By implanting these tags inside a physical
object, the object gives the power to be
monitored and controlled remotely through the
Internet, with the help of a smartphone. This
eliminates the need for human people to
constantly enter and monitor data. Instead,
objects can work directly with each other and
can collaborate without the need for a person
to link them together [9].
3. Smart Tags/Cards for Things Authentication and Data Integrity
In a retail or supply chain management
integrated solutions, RFID – vicinity/proximity
tags or cards will be attached to the products
and things, in order to store data and metadata about the products. The sensors will
read or modify the data stored in RFID labels
attached to the things. In order to provide
authentication and data integrity, the solution
will have an authentication procedure that
requires minimum of processing and power
consumption, but in the same time it will be
strong enough to avoid security pitfalls.
The minimum authentication model will require
a mechanism similar with CRYPTO1 from
Mifare 1K/4K proximity cards and a higher
secure model would be inspired from Sony
FeliCa cards and VISA/Mastercard DDA
(dynamic authentication) procedure from
banking cards (MULTOS or Java Card).
Mifare DESFire tags/cards have only
contactless interface for communications and
they are fully compliant to the ISO/IEC14443A
(1-4). They have 7 bytes UID (“Double Size
UID”) and from point of view of CPU & OS,
there are the following features:
- Asynchronous CPU core
- (3) DES coprocessor
- Fixed Command Set
- No Customer ROM codes
The Mifare DESFire file-system is able to
handle:
- up to 28 application / card
- up to 16 files / application
- up to 14 keys / application
- 1 master-key for card maintenance
- Plain, (3)DES encrypted, or MAC-ed data transmission
- On-Chip Backup management
This section presents an authentication
procedure specific to Mifare DESFire
tags/cards that have certain particularities and
requirements. An improved procedure should
be
sufficient
for
RFID
tags/cards
authentication and it is presented as Java
source code statements for non-sensitive
operations (the complete source code may be
obtained from the authors):

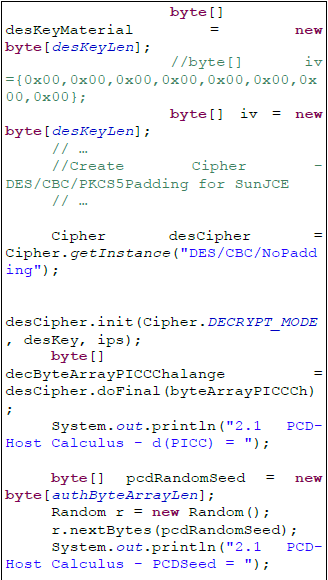


The data and meta-data for products/things
might be stored in files inside the file system
memory layout and they will be encrypted with
the session key negotiated during the
authentication procedure.
We can mention also the need of security
outside the authentication, especially in the
banking field, where are some applications
that do not require users' authentication.
Generally, these applications are accessed
internally, by the bank employees, and the
access is provided from other applications,
based on single-sign-on principles. In such
situations, the security must be ensured
through restricted access rights on mainly
resources and by monitoring users' access
with the help of log files [10].
4. Conclusions
In 2020 there is estimation that will be 50
billion IoT devices in the market. At least all
the consumers of “Java enabled” and
Embedded Linux smart objects will be in the
main target group for open source solutions.
The smart objects are processing the data
collected from sensors and for instance, from
RFID tags/cards. The authentication process
is an important approach taking into account
NFC and RFID domains expansion.
Besides the authentication process of RFID
tags/cards by the IoT sensors, the paper
represents the basic know-how for developing
a proof of concept that will demonstrate how
the RFID/NFC tags/cards are written with
meta-data information, and then periodically
tags/cards
area
read
by
RFID/NFC
reader/writer devices (sensors), in order to do
the things tracking. The obtained information is
securely and collaborative aggregated into a
unified data model and processed using
distributed computing methodologies over “big
data”.
The proof of concept project results may
include:
- The formal models, architecture, REST/Web-services/communications protocols and M2M data-structures;
- The beta version of the software libraries that implement products/services tracking and clustering:
- sensor control using devices SDKs; the reading/writing of the data formats from/in RFID vicinity/proximity tags/cards and optionally, reading 2D barcodes of the products/services;
- “big data” processing and semantic parsing, via distributed computing model and implementation, using embedded devices/boards (Internet of Things „smart objects‟, e.g. Raspberry-PI board) for cloud micro-instance deployment and standard PCs/laptops;
- secure communications from sensors to „smart-objects‟ via IoT Service Gateways.
During the development of the proof of
concept project, we estimate that we will
create
pre-requisites
to
offer
Java
implementation for Smart Object API, to
enhance
the
existing
security
and
communications
protocols
for
REST
Interface/Web-services, and improvement of
M2M/IoT data models plus value added
services for existing and new IoT deployed
“silos”-es.
Acknowledgement
Parts of this paper were presented by the
authors at 6th International Conference on Security for Information Technology and Communications (SECITC'13), June 25-26,
2013, Bucharest, Romania.
References
![]()
This work is licensed under the Creative Commons Attribution 3.0 Unported License. This page must provide all available authorship information.
Public domainPublic domainfalsefalse
- ↑ Cristian Toma, Cristian Ciurea, Ion Ivan – Authentication Issues for Sensors in IoT Solutions, Proceedings of the 6th International Conference on Security for Information Technology and Communications (SECITC'13), June 25-26, 2013, Bucharest, Romania, ASE Printing House, ISSN 2285-1798, ISSN-L 2285-1798.
- ↑ Wikipedia, Internet of Things, Available at: http://en.wikipedia.org/wiki/Internet_of_Things
- ↑ Open Smart Cities I: Open Source Internet of Things, Available at: http://observatorio.cenatic.es/index.php?option=com_content&view=article&id=807:open-smart-cities-i-open-internet-of-things&catid=94:tecnologia&Itemid=137
- ↑ Michael Koster, Data models for the Internet of Things, Available at: http://iot-datamodels.blogspot.ro/
- ↑ Ibid.
- ↑ Ibid.
- ↑ Tom Vu, The Internet of Things: Inspiration and Requirements, Available at: http://blog.makezine.com/2013/04/18/the-internet-of-things-inspiration-and-requirements/
- ↑ Chad Brooks, The Internet of Things: A Seamless Network of Everyday Objects, Available at: http://www.livescience.com/38562-internet-of-things.html
- ↑ Ibid.
- ↑ Ion Ivan, Cristian Ciurea – Security Aspects of Collaborative Banking Systems Applied in Economy, Journal of Mobile, Embedded and Distributed Systems, Vol. 3, No. 4, 2011, ISSN 2067–4074.